Implementing a Data Bodyguard For The Cloud
Re-posted from Cyber Defense Magazine.
Modern security solutions – be they application, endpoint, IoT-focused, etc. – have evolved. Security has been shifted both left and right. However, data breaches continue to increase. The reason is very simple: almost all security solutions focus on protecting and monitoring the infrastructure or the device, but not the data.
Think about the first family of the U.S. They have an entire security team focused on protecting them, no matter where they go. Organizations need a similar approach to keeping data safe – think of it as a “data bodyguard” or protection that moves with your data. Data is any organization’s most important asset, and yet time and time again, legacy solutions are failing to protect it.
What cybersecurity gets wrong
Data breaches continue to take place all the time, despite far more awareness than ever before and a proliferation of cybersecurity solutions. In fact, according to IBM’s 2022 Cost of a Data Breach report, 83% of organizations studied have had more than one data breach. And these breaches are getting more expensive, reaching an average cost of $4.35 million in 2022, up 2.6% from the prior year.
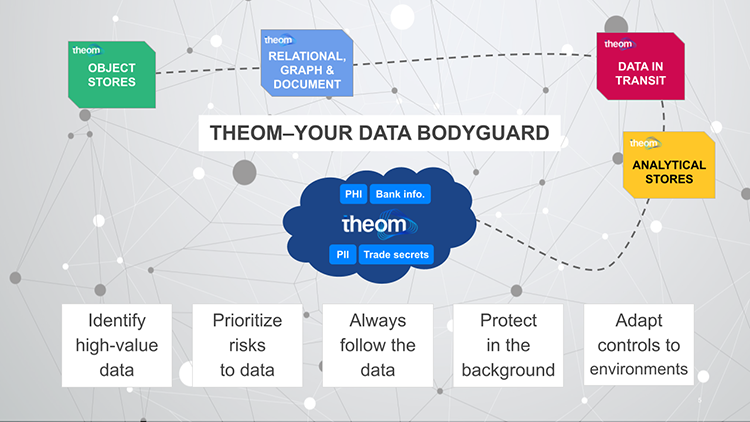
The biggest challenge stems from how data is being protected in most organizations. It’s the most important asset for almost any organization, and yet security solutions are traditionally failing to really focus on it. There is no shortage of cloud security, endpoint security, application security solutions and the like – but these still don’t solve the major challenge of protecting your data as it moves or gets copied, because they are oblivious of what they are supposed to be protecting. In these cases, the protection or controls you have in place don’t necessarily follow that data. That’s why breaches happen.
What’s needed is a way to protect your data as it moves from location to location – in a way that’s affordable and operationally easy to use, without causing more stress on organizations already grappling with limited budgets and the ongoing cybersecurity skills gap. In addition, enterprises need an anti-fragile zero trust solution focused on data. A working zero trust system has zero implicit trust, and it puts data in the center and then builds protection outward.
Security that moves with your data
Breaches keep happening because we’re not watching the data. Instead, we’re focusing on applications, endpoints and so on. Most people know they have a problem when it comes to protecting their data, and part of the issue stems from not knowing how to prioritize the data. To protect it, you need a better way to understand the value of that data, and most companies don’t have an internal crawler that indexes their own data.
And it’s not just about the data – it’s also about who is trying to access the data. For instance, in a financial services organization, imagine that certain sensitive financial data can only be accessed by financial analysts inside the U.S. You need the right controls and rules in place that govern who can access what data, when and from where. This is tedious and time-consuming work for humans; automation is a better solution.
An anti-fragile, data-centric approach
A best practice is to implement what’s known as an anti-fragile, data-centric zero trust system:
- Establish “data intelligence”: Know the data you are trying to protect. If you do not know what you are trying to protect, you will never successfully protect it. This includes visibility of cloud data stores, data lakes, your data warehouses – where your data is stored and data-in-transit points (message Queues/APIs), etc.
Establishing data intelligence entails these steps:
- Create a protection surface. An effective protection surface (or minimal attack surface) can only be built by putting data at the core and defending outward from it.
- Use an automated tool to discover the data, catalog it, establish the criticality and business value of it, and map the data flows. This requires continuous data discovery, data classification (standard taxonomy and custom taxonomy), and data flow/lineage mapping.
- Using the above two steps as input apply the principle of least privilege of access all the way to data tables and granular data store constructs. Automating this step and marrying it with the policy guardrails is critical to create an anti-fragile system.
- Deploy an automated tool to discover and baseline who (electronic or human) accesses what data.
- Asset and alert prioritization: Automatically establish the priority of risks based on business criticality of data. You need an automated way to essentially put a financial or business value on your data to help prioritize it. How important is each piece of your data? And who is accessing it? What are their roles? Automatic data centric prioritization means you don’t have a runaway security budget in terms of hiring more people and buying unnecessary tools.
- Coarse business policy guard rails for security and compliance: Coarse policies are key to anti-fragile zero trust systems. Set up very simple to express and coarse business policy guardrails to get continuous data assurance and data compliance. You can start to put in the right controls and then prioritize the risks to the various stores of data. These rules should be oblivious of the data store or data in motion constructs. Enforce the rules through a SIEM/SOAR where data is stored, or over which APIs data is moved.
- Workflow integration and harmonization: Enforcement of the data assurance, compliance and protection guardrails must be done using a SIEM/SOAR integration.This step ensures you have investment protection and also do not have to re-train the cyber security staff. Automating the prior steps eliminates the need to train cyber security staff on data technologies.
- Monitoring: This enables continuous system improvement for a data-centric, anti-fragile zero trust system. It provides a historical timeline view-based tracking of data access and relationships between different security attributes of data. Monitoring helps with high-quality incident reviews and also forms a solid foundation to drive a feedback loop.
Defending the core
Building defenses outward around a core of data is a common-sense approach to data security. Cyber attackers are going to get in, but you can take steps to ensure they can’t access your valuable data. This is the benefit of implementing a data-centric, anti-fragile zero trust system. Use the approach outlined above to deliver a zero trust approach to data protection.

