Theom ensures organizations can implement Zero Trust Principles in a data-centric manner ensuring only the right people can access the data at the right time.
Implement Zero Trust focussed on data and not just the perimeter

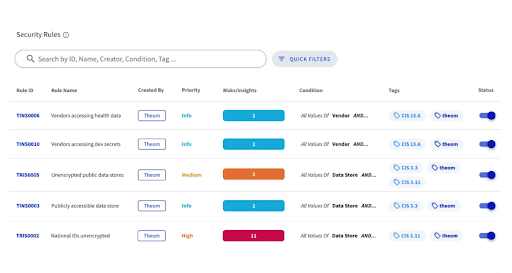
Organizations can achieve a data-centric Zero Trust approach and implement Zero Trust data security using Theom. Here's how Theom can enable organizations to embrace Zero Trust principles for data protection and governance:
1. Data-Centric Zero Trust:
- Theom enables a data-centric approach to Zero Trust, focusing on protecting the data rather than solely relying on perimeter-based security.
- It ensures that access to sensitive data is strictly controlled and granted based on the principle of least privilege.
- Theom's granular access control capabilities allow organizations to define specific permissions and restrictions for data access, ensuring that only authorized individuals can interact with the data.
2. Enhanced Access Controls:
- Theom enables organizations to implement fine-grained access controls at the data level, ensuring that data is only accessible to users and applications with legitimate needs.
- Access controls can be defined based on user roles, responsibilities, and specific data protection requirements.
- Theom's AI-driven algorithms continuously monitor data access events, enabling real-time enforcement of access policies and immediate detection of unauthorized access attempts.
3. Continuous Monitoring and Anomaly Detection:
- Theom leverages advanced analytics and behavioral monitoring to establish baselines of normal user and entity behavior.
- Any deviations from these baselines are flagged as anomalies, triggering real-time alerts for potential security risks.
- This continuous monitoring allows Theom to detect and respond to suspicious activities, ensuring that data access is consistently monitored and verified.

4. Data Encryption and Tokenization Posture:
- Theom supports posture for data encryption and tokenization techniques, ensuring that sensitive data is protected at rest and in transit.
- Encryption mechanisms safeguard the confidentiality and integrity of the data, mitigating the risk of unauthorized access or data leakage.
- Masking/Tokenization techniques can be applied to replace sensitive data elements with randomly generated tokens, reducing the exposure of sensitive information. Theom extends the native capabilities of data stores to ensure tokenization and masking happen right.
5. Complete visibility of Identity and Access:
- Theom integrates with IAM solutions to ensure user identities and access credentials are properly managed and authenticated.
- IAM solutions provide centralized identity management, authentication, and authorization capabilities, enabling organizations to establish a strong foundation for Zero Trust.
6. Operational Hygiene on Identity/Access:
- Theom ensures only the right people have access to the right data at the right time. With workflows to reduce over-provisioning and shrink-wrapping access permissions, Theom ensures principles of least privilege is adhered to within an enterprise.
7. Continuous Risk Assessment:
- Theom conducts continuous risk assessments by monitoring data access patterns, detecting unusual activities, and evaluating the associated risks.
- Risk assessments enable organizations to identify potential vulnerabilities and take proactive measures to address them, reducing the likelihood of data breaches or unauthorized access.
8. Audit Trails and Forensics:
- Theom maintains comprehensive audit trails of data access activities, including user actions, data queries, and system interactions.
- These audit trails enable organizations to conduct post-incident investigations, perform forensics, and ensure accountability.
- Theom's advanced logging and reporting capabilities provide organizations with the necessary visibility into data access events, supporting compliance efforts and facilitating incident response.
9. Sharing Governance:
- Theom facilitates secure data sharing through various mechanisms, including direct shares, clean rooms, and data exchange marketplaces.
- Direct shares: Theom allows organizations to establish controlled and secure data sharing with authorized external parties, ensuring that data is only accessible to approved recipients.
- Clean rooms: Theom enables the creation of clean rooms where external parties can securely analyze and work with sensitive data without accessing the underlying raw data. Theom ensures that data governance policies are extended into the clean room environment, maintaining control and compliance.
- Data exchange marketplaces: Theom supports secure data exchange marketplaces, where organizations can participate in trusted platforms to share and monetize their data assets securely. Theom ensures that data governance and security measures are enforced during the data exchange process.
- By incorporating governing sharing options like direct shares, clean rooms, and data exchange marketplaces, Theom extends its Zero Trust data security capabilities to enable secure collaboration and data sharing while maintaining strict control over data access and adhering to data governance policies.
Theom ensures zero trust is done right, focusing on data and access and not just the perimeter.

