Take control of your cloud data.
Detect and stop breaches, now!

Why Theom?
Data governance is usually defined as a set of policies that apply to the entire data lifecycle from ingestion to disposal. Observing/ cataloging data and encapsulating a desired state in policies are usually foundational steps at the beginning of the data journey toward AI. However, expressing intent through policies can’t be done in isolation. To be of any value, policies need to be enforced and continuously updated based on actual vs intended behavior. In a world with rapidly rising ransomware, insider attacks, and other sophisticated attempts at exfiltrating data, enforcement quickly requires deep security expertise. For most data store vendors, this expertise is either in its infancy, as this is not their core domain, or it sits far away in dedicated security groups where data expertise does not exist. As outlined in greater detail below, traditional security architectures make it even harder to protect data because of their perimeter focus. To overcome these shortcomings, Theom uniquely integrates the definition of intent through policies with deep enforcement expertise based on sophisticated AI-based security.
Between 30%-40% of all users have their data deployed across more than one of the traditional data store providers. It is increasingly common to see Databricks and Snowflake in the same accounts. It does not mean they split the data estate of a user evenly, but they coexist. Data governance has to be applied consistently across all data stores to minimize attack surfaces. Theom, a dedicated data access governance and security platform, can uniquely consolidate all data stores under one pane of glass, avoiding siloes and the unneeded specialization of teams.
One quick word on AI. Currently, AI (esp. generative AI) and LLM are attached rather liberally to anything that generates some sort of intelligence from data. The Theom founders have productized AI techniques for years at companies like Google and Cisco, and they have implemented newer approaches as they came out of research. At Theom, we are currently using a wide spectrum of technologies, from simple machine learning to more sophisticated approaches based on generative AI or generative adversarial networks (GAN). Our AI expertise has also resulted in new approaches to secure AI models, and we can’t wait to productize and release our own “dog food.” Always contact our founders or engineers for a deeper discussion on the topic. They always enjoy the exchange with customers and like-minded practitioners.
The need for Theom becomes even more obvious upon reviewing the current state of the security market. Theom does not only uniquely combine Data and Security in one platform – it also comes with a very different security approach that is much more suited to the challenge at hand.
Every major enterprise has dozens of security products and suites, and consolidating technologies into increasingly comprehensive platforms offered by a handful of vendors is a major trend. What are the current offers to address data access governance in the unending labyrinth of security products that all come with sophisticated acronyms? The surprising answer is that there aren’t any solutions, as traditional security has been focused on strengthening the perimeter, i.e., keeping bad actors out. However, as illustrated above, data governance will require an insider’s view. As data governance is closely attached to the data, it is only logical to have data governance and its enforcement sit next to it. Co-location with the data will also avoid data transfers (including metadata), increasing the overall system's security. Thinking of data and AI as representing a paradigm change is generally useful. Just like the advent of the cloud required security architectures to evolve beyond on-prem, Data and AI need new dedicated platforms to provide the security and trust for the new data economy. Furthermore, these new platforms will also accelerate the adoption of data and AI as they break down silos and reduce the diffusion of responsibility between an organization's Security, AI, Data, Risk, and Compliance. Lastly, these new platforms also need to integrate into existing SIEM and other visibility platforms to include data and AI security into a holistic security framework.
Below, please find a detailed checklist of why traditional security approaches fall short when it comes to data:

Security Perimeter, Firewalls, EDR solutions: Traditional security measures often focus on securing the perimeter, i.e., the network and the endpoints. However, as the data is the ultimate target, security measures should be data-centric. When security sits outside the SaaS data lake, it can be bypassed, allowing attackers to access the data.
Phishing Attacks have only grown in volume and significance: Despite advancements in security, phishing remains a significant threat. A phished user can gain legitimate access to the system, bypassing many security measures. Once inside, they can manipulate the system, disable notifications, and create backdoors while appearing as legitimate users.
Data sharing leads to abuse and loss: Businesses innovate with data; however, when data is shared using the new data economy (Snowflake, Azure Synapse, Databricks), it's not governed or monitored with the current set of tools. This leads to unauthorized/unwanted access, potential data breaches, and loss of reputation. This can also cause reluctance to embrace new technologies and innovate quicker.
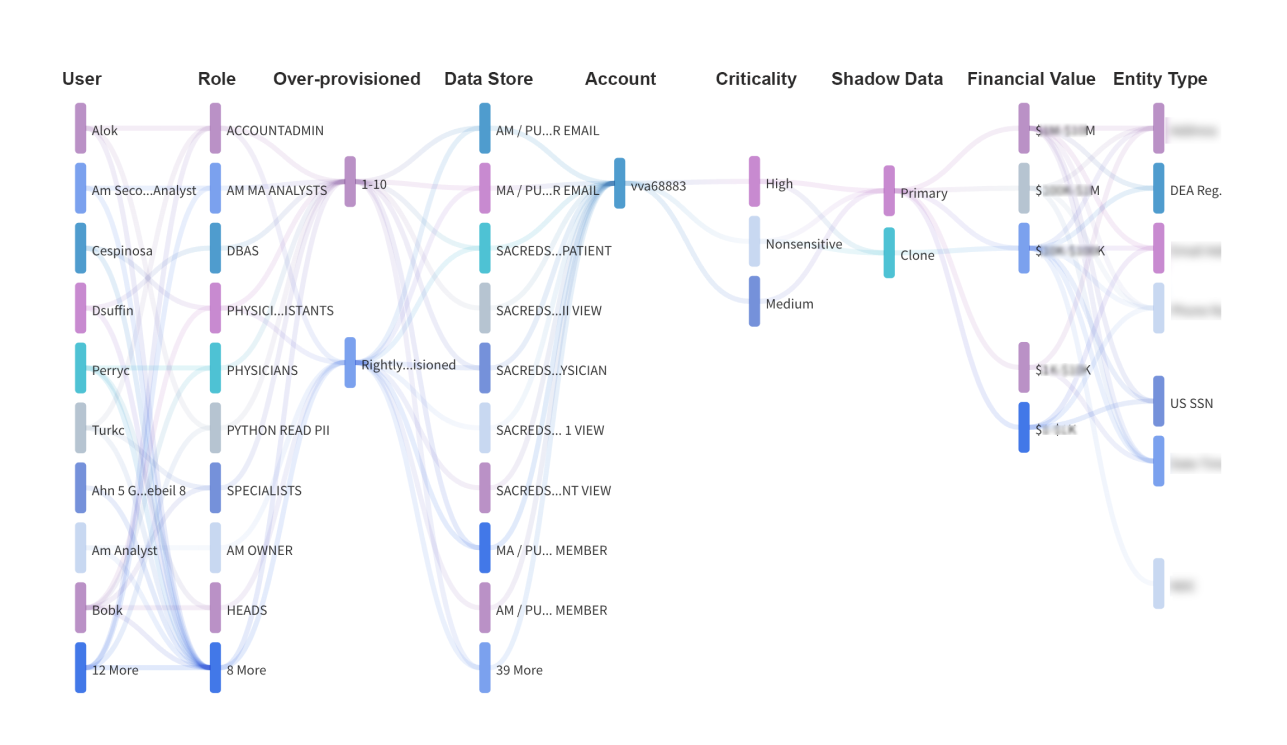
Insider Threats go unnoticed, leading to data loss: The current state of security often needs to address insider threats adequately. A malicious insider or a compromised account can change network policies, clone tables, and exfiltrate data. Because an authenticated user performs these actions, they can often evade detection.
Data Exfiltration: Data exfiltration can often go unnoticed, especially through non-traditional methods like cloning and dumping cloned tables. Current security measures may not be equipped to detect and prevent such sophisticated data exfiltration techniques.
Covering Tracks: After carrying out malicious activities, attackers often cover their tracks to avoid detection. This could involve deleting logs, disabling notifications, or reverting changes to network policies. Current security measures may not be able to detect or prevent such activities effectively.
Real-Time Detection and Response: Many security solutions lack real-time detection and response capabilities. This means the damage may already have been done when a breach is detected.



Prevent data risks and detect insider threats
Secure and Govern your data lakes: Theom offers unique data-centric security for platforms like Snowflake and Databricks, making it the only tool in the market with this capability. By protecting data, not just the systems and networks where it is stored, Theom ensures security throughout the data lifecycle, irrespective of its location. This approach provides organizations with improved visibility and control over sensitive data, equipping them to identify and respond to potential security threats. Theom operates within your data clouds, building intelligence by comprehending both encrypted and clear text data.
Secure data shares/clean rooms and data exchanges: On Snowflake and Databricks, Theom secures your data in whichever way you share.Theom offers robust security solutions for data shares, clean rooms, and data exchanges, specifically designed to operate with platforms like Snowflake and Databricks. As the industry's only holistic data-centric access governance platform, Theom continuously evaluates access from your trusted workforce/external partners and applications on cloud data stores. This ensures the security of clean rooms and data shares, empowering enterprises to safely share and innovate using their data with first parties and vendors. To prevent data abuse and maintain security, Theom implements various measures, particularly within data lakes, for collaborative analysis.
Combine preventive and detective security: Theom provides a comprehensive tool for both preventive and detective controls, covering Data Access Governance (DAG) and Data Security and Privacy Management (DSPM) with remediation capabilities via Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) integration. This holistic approach helps detect live data breaches that standard DSPM tools might not cover.The platform’'s primary focus is ensuring correct data access - the right people should have access to the right data at the right time, mitigating the risk of data breaches and adhering to data protection regulations. Theom enables enhanced data visibility, enabling early intervention before incidents occur and helping to improve your organization's insider risk management, access governance, and security initiatives.
Theom integrates contextual, behavioral, and security monitoring into a single platform, offering a comprehensive view of insider risks from all perspectives. It applies the MITRE ATT&CK framework for threat detection, operating natively on data stores across various cloud platforms.
Furthermore, Theom uses an API-first approach to seamlessly integrate with a wide variety of IT systems and applications, such as identity and access management tools, SIEM, SOAR, and other custom tools. This ensures a unified and consistent approach to access governance and responding to attacks across the organization, reducing the complexity and overhead of managing multiple security solutions.
Business customizations
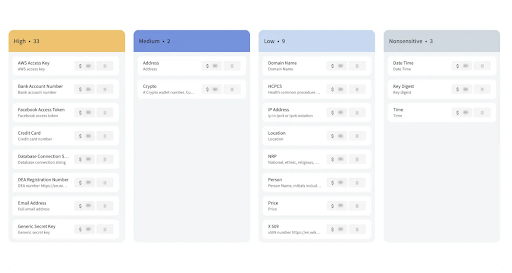
Theom offers a tailored understanding of your business needs and customizations. It provides cloud data security solutions specifically defined for business data and identity. Its unique approach centers on data-focused workflows, visually representing cloud security risks and offering mitigation measures. These workflows operate harmoniously across all types of data store technologies, ensuring a seamless security process regardless of your chosen platform. Theom facilitates cross-cloud and cross-data store support, which means it can manage and secure data across various cloud services and storage solutions. It also offers the capacity to establish custom classifications. This feature allows you to design taxonomies that align specifically with your enterprise or industry standards, which can then be mapped accordingly within the system.The platform also identifies and maps anomalous data accesses according to the MITRE ATT&CK framework. This approach wrt cyber adversary behavior aids in better understanding threat actions. Furthermore, Theom's features can be API integrated into any enterprise-specific dashboard, providing a flexible and cohesive security experience. Theom incorporates a custom data access governance rules engine. This empowers enterprises to define and implement their policies, creating a personalized layer of security control. Thus, with Theom, organizations have a comprehensive and adaptable solution for managing their cloud security needs.
No data leaves the customer's environment
Theom ensures that no data leaves the customer's environment, providing discovery, classification, risk analysis, governance, and protection of cloud data within the confines of the customer's cloud. It constructs security intelligence inside the customer’s data cloud, bringing computing close to where data is stored. By embedding itself within your data clouds, Theom presents a robust security solution that is challenging to circumvent.
Low operational costs, no operational staff retraining: Theom offers an efficient solution with low operational costs and no need for operational staff retraining. It provides efficient and cost-capped data classification, eliminating hidden data transfer costs or egress charges. With a fast and fully automated setup process, Theom offers value within just 2-3 hours. It also integrates seamlessly with existing tools, offering supported modules for IT Service Management (ITSM) platforms such as ServiceNow and Jira and Security Information and Event Management (SIEM)/Security Orchestration, Automation, and Response (SOAR) systems like Splunk and Azure Sentinel.
Theom is deployed within the customer's cloud environments and scales to the customer’s growing data needs and sizes with no additional cost overhead. With no impact on the customer’s current running applications, Theom gets deployed in minutes bringing the overall time to value to hours. Theom does not cause any sovereignty or regulatory concerns after deployment.

