Enrich visibility with relevant context for faster MTTR
you can't protect what you can't see!
Data security observability

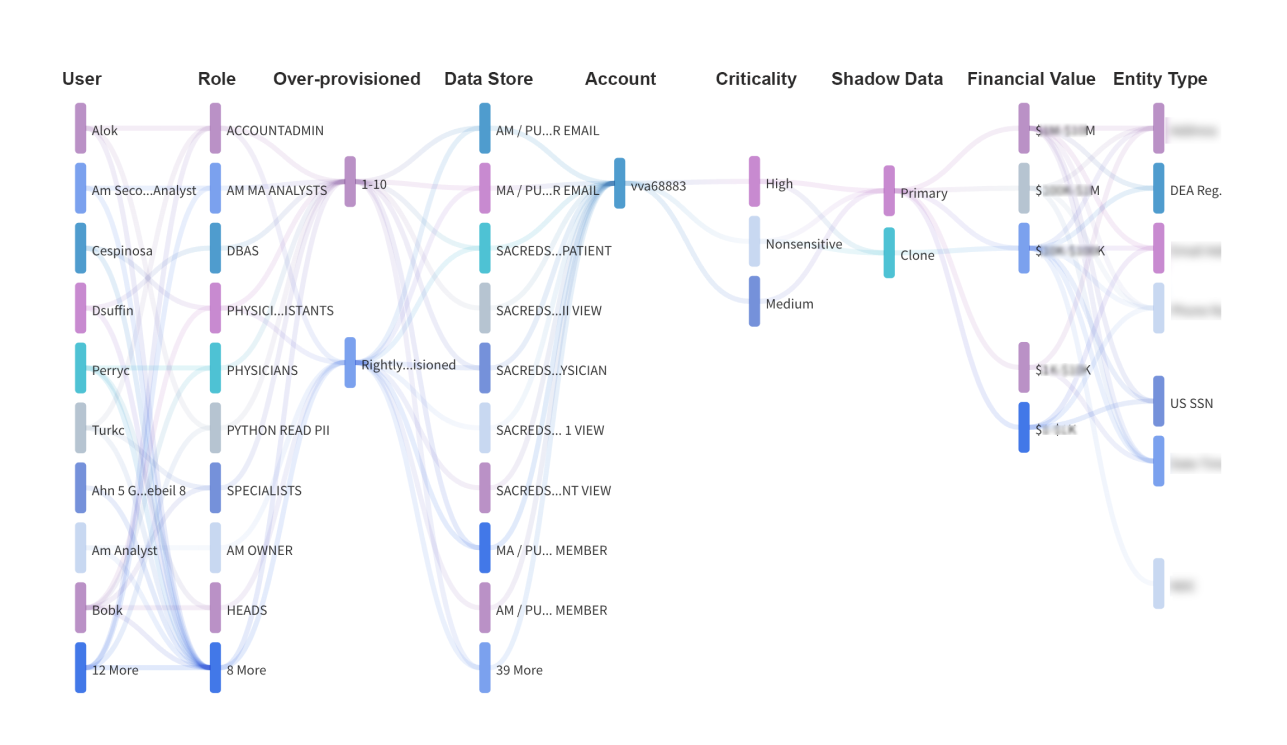
Providing a comprehensive overview of the data is usually where the data governance journey starts. What data do I have, and where? Who is accessing it? From where? The permutations are nearly endless. Configuring views of the data and enriching them with the context in real-time creates the foundation to manage and monitor the data governance/security posture actively. It also provides the overview needed to react to alerts as they happen with the fastest MTTR possible.
Theom discovers all the data inside data lakes and warehouses, cloud object stores, and databases. The high accuracy of the discovery process also leverages Theom’s architecture as being embedded with the data (and running inside Snowflake or Databricks, for example), allowing Theom to see every query in the clear vs. relying on the interpretation of encrypted data. The platform provides a detailed topology of all the data and how it is accessed by human and machine users in one consolidated view.
Theom evaluates every attempt to access data against existing (static) rules and (dynamic) baselines derived from machine learning.
The platform allows organizations to define fine-grained access permissions for each user, group, or role – down to individual cells or columns. Additionally, machine learning models continuously observe access activities in great detail to learn what “normal” access looks like. Both violations of access permissions and deviations from these AI baseline access patterns – frequently indicative of insider or phishing attacks - trigger automatic alerts and other user-defined actions (all the way to shut down a user instantly).
Theom also automatically detects where data sources are overprovisioned and recommend corrective actions. Data sources are labeled as “overprovisioned” if they allow access to users that should not have access - be it that access permission has not been updated or should have never been authorized.