Complete data and access visibility for Snowflake, Databricks, and Azure data stores.

Not all data is created equal. The value of data is ultimately determined by the business cases they feed into. However, independent of business cases, certain data enjoys special protection by law/compliance rules, given their sensitive nature. Frequently, the sensitivity is more than just a one-dimensional construct, as in the case of GDPR, where the location of the data is of critical importance. Modern data governance platforms automatically classify data and assign values based on deep reads and NLP. Conflating data sources with their value and risk profile will highlight critical risks and guide remediation efforts.
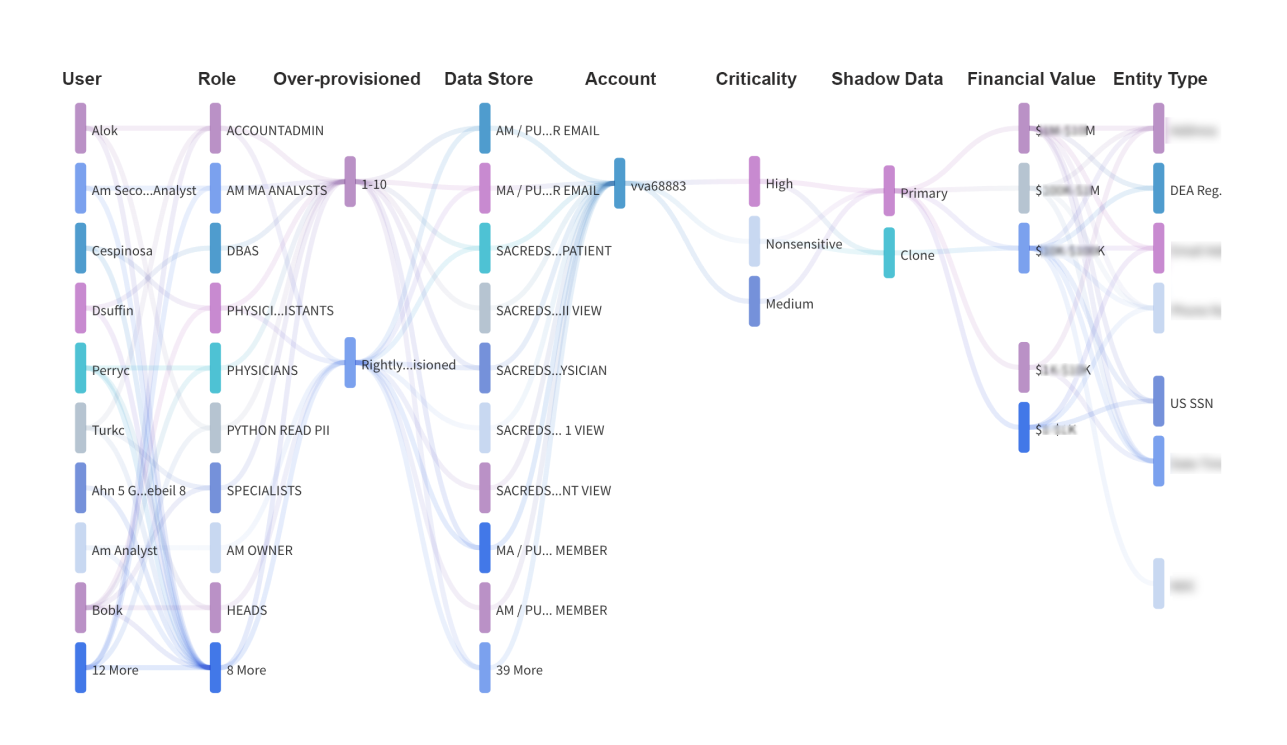
The questions “What data?” and “Who has access?” become even more complicated when the aperture is narrowed from the holistic to the atomic level, as the unit of labor for data access governance is rarely an entire data warehouse but individual cells or columns. Defining access rules down to individual cells has become necessary, not just in enterprises but inter enterprises where hundreds of millions of records are exchanged in clean rooms by allowing customers unique and fine-grained access to pieces of the same data set. Access rules are rarely static: employees and customers turn over, organizational charts change, and business processes get reorganized - updating systems is frequently challenging. Additionally, access rights get frequently defined rather loosely, i.e., employees receive access based on a role or their position in the organization chart and not based on the data itself and the business outcomes it drives. Every over-provisioned account is a substantial security risk.

Understanding who can access the most sensitive data within the enterprise is a gap in today’s security tools. Further, understanding the reality of access, if the provisioned privilege for a user was used or not, is a much bigger issue. Theom's granular access control engine allows organizations to define specific permissions for each user, group, or role. This prevents unauthorized access and maintains a strict level of security by limiting access to only those who require it for their role. Administrators can easily configure and modify permissions as needed, ensuring a flexible and dynamic approach to access governance.
Theom provides visibility into data, with automated discovery and accesses that are accessing data all within a single tool, agentless and deployed in minutes. The entire visibility is available within a few hours of Theom deployment.

