Overview

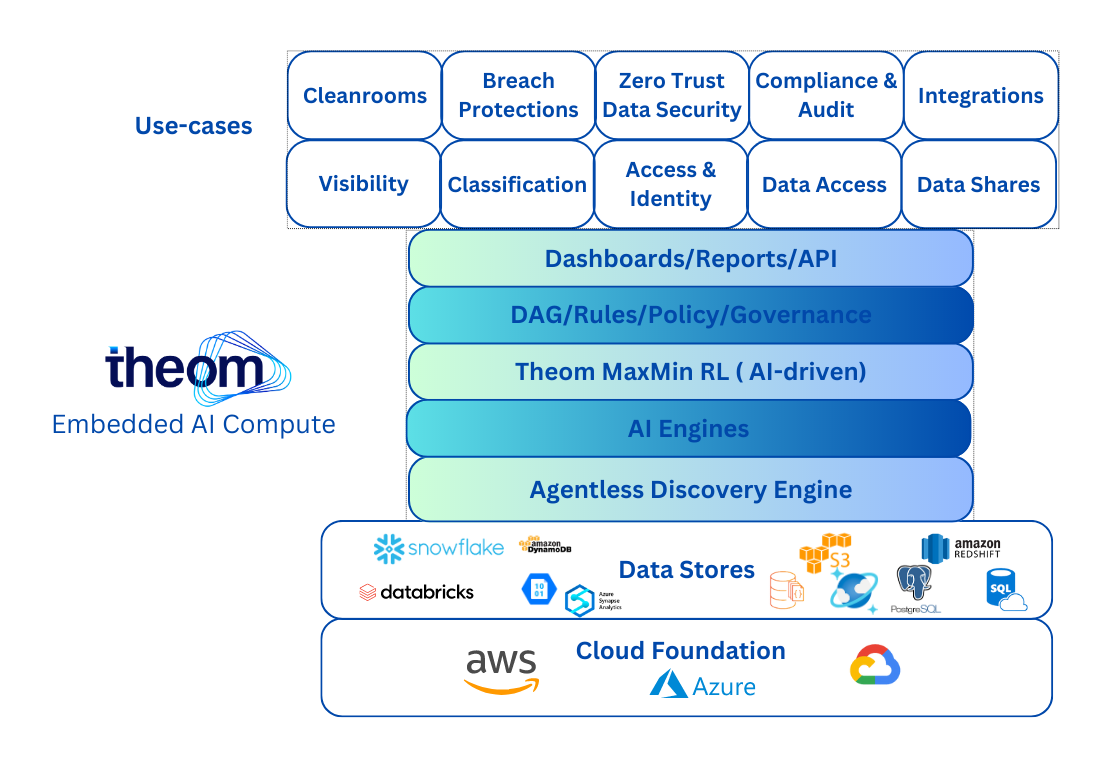
The Theom AI Platform
The Theom AI platform combines core data governance capabilities that run on a common core foundational and analytical services framework. The platform modules run within the same contextual wrapper avoiding continuous on- and offboarding, breaking down technical and organizational siloes. While different teams and personas might have different views on the data, they all still look at the same underlying data/context while running their specific analytics against it. The platform is open and extensible, ie. all foundational /analytical services and modules can be dialed in via API calls. Integrations with eco-system partners like Microsoft, ServiceNow and Databricks are already available. Theom will continue to expand the breadth of its platform into other compelling use cases while also empowering customers and partners to adopt the platform to their specific needs.
Dashboards/Reports and API
Theom offers a plethora of dashboards and reports out of the box, depending on use cases. Furthermore, Theom provides customers and partners with a framework to customize dashboards, reports, and entire workflows. All Theom functions up and down the stack can be integrated into applications via API calls.
DAG, Rules/ Policy/ Governance Engine
Data Governance defines the traffic rules for data. Ingesting, defining, and enforcing rules is at the core of many governance-related activities, as the definition of good behavior is the first important step in identifying deviations and abnormalities. Theom’s rule-based engine is infinitely scalable and can ingest complex rules from even the largest environments. Furthermore, Theom offers an editor for the easy definition of fine-grained rules. Rules can also be auto-generated by AI Engine to remediate problems or fix inconsistencies. Generative AI will increasingly take over the role of generating rules based on user intent.
MaxMin, RL
Theom has developed proprietary technologies to keep its footprint inside a data store amazingly small. We have seen customer scenarios where less powerful data governance frameworks used up six XL instances. At the same time, MaxMin ran Theom in only one of the smallest instances with no performance penalty. This translates into immediate operating cost savings. It is truly Maximum Impact at Minimum Resource Consumption.
Theom’s AI Engines:
AI engine developed by Theom leverages cutting-edge AI techniques such as reinforced learning, GAN (Generative Adversarial Networks), GenAI, and NLP-based transformer technologies. This advanced engine is designed to enhance Theom's capabilities in attack detection, behavior anomaly verdicts, breach simulation, breach detection techniques, and classification tasks.
AI engine comprises the following key capabilities:
- Reinforced Learning with Human Feedback for Attack Detection and Behavior Anomaly Verdicts:
- AI Engine utilizes reinforced learning algorithms, which allow the AI engine to learn from interactions with its environment and make informed decisions.
- In the context of Theom, this approach enables the engine to detect attacks by continuously analyzing data access patterns, system interactions, and user behavior.
- AI Engine incorporates human feedback into the learning process, benefiting from the expertise of security professionals who provide guidance and validation for attack detection.
- Combining reinforced learning with human feedback makes Theom's AI engine adept at recognizing attack patterns, identifying behavior anomalies, and providing accurate verdicts. - GAN for Breach Simulation and Finding Techniques for Breach Detection:
- AI Engine employs Generative Adversarial Networks (GANs), a machine learning technique that consists of two neural networks: a generator and a discriminator.
- The generator is trained to generate synthetic data that mimics real-world breaches or attack scenarios.
- The discriminator is simultaneously trained to differentiate between real and synthetic data, forcing the generator to improve its output continually.
- By utilizing GANs, Theom's AI engine can simulate breach scenarios and identify potential weaknesses in the system, helping organizations proactively address vulnerabilities and enhance breach detection techniques. - Transformer based on BERT for Classification:
- AI Engine utilizes transformer-based models, specifically leveraging techniques based on BERT (Bidirectional Encoder Representations from Transformers).
- Transformers have revolutionized natural language processing (NLP) tasks by capturing contextual information and relationships within textual data. Theom extends transformers for custom data taxonomies understanding business context.
- Theom's AI engine employs transformer models to perform classification tasks, such as categorizing data access events, behavior anomalies, and security incidents.
- By leveraging BERT and transformer-based architectures, AI Engine enables accurate and contextual classification, enhancing Theom's ability to identify and respond to potential threats. - Generative AI-based remediations:
- Theom uses Generative AI-based technology to develop automated remediations for every attack/data risk.
- The remediations are natively available as extensions with the customer’s SIEM/SOAR tools.
- Theom’s remediations are native to the data cloud where the attack or violation was detected. - Governance and Attack Detection based on AI:
- Theom's AI engine incorporates governance principles into its attack detection and security operations.
- The engine follows predefined governance policies, rules, and compliance standards to ensure its actions align with organizational and industry requirements.
- By utilizing AI-driven attack detection, Theom enhances its ability to identify and respond to security threats in real time, enabling proactive incident response and reducing the impact of potential breaches.
- The AI Engine continuously learns and adapts to evolving attack techniques, improving its detection capabilities and staying ahead of emerging threats. - Cost-effective Scalability:
- AI Engine is designed to efficiently utilize available resources, allowing Theom to scale within customers' environments while minimizing costs. It has cost governance capabilities baked into the computation substrate.
- The engine optimizes resource allocation and computational efficiency, ensuring it can handle increasing data volumes and workloads without incurring significant infrastructure expenses.
- This cost-effective scalability enables organizations to grow their data environments within the cloud without the burden of excessive resource allocation. - Maximum Impact with Minimum Resources:
- AI Engine leverages advanced techniques and algorithms to maximize its impact on threat detection, behavior anomaly verdicts, breach simulation, and breach detection.
- By efficiently utilizing available resources, the AI Engine achieves powerful results with minimal resource requirements.
- This approach enables organizations to leverage Theom's AI capabilities without straining their infrastructure, allowing for maximum impact while minimizing operational costs. - Seamless Scalability as Customer Data Grows:
- As customer data grows within cloud environments, AI Engine seamlessly scales alongside the expanding data volumes and workloads.
- The engine is built to handle large-scale data environments, ensuring that Theom remains effective and efficient as the data landscape evolves.
- The scalability of AI Engine allows organizations to maintain consistent security coverage and performance, regardless of the size or complexity of their data infrastructure.
AI Engine’s capabilities within Theom enable organizations to leverage advanced techniques in breach simulation, behavior anomaly detection, and classification to enhance their overall security posture and protect their sensitive data. By incorporating these advanced techniques, AI Engine enhances Theom's governance-based approach to attack detection, behavior anomaly verdicts, and overall data security, empowering organizations to defend against threats and maintain a robust security posture proactively.
Theom’s Agentless Discovery Engine
While current security architectures are mostly focused on perimeter defense, Theom is embedded into the data store sitting right next to the data and seeing every query of the data in the clear (and not in encrypted gibberish if you are outside the data store). Seeing and analyzing every interaction with the data puts us in the pole position to deliver unique insights and actions across the entire spectrum of modules, from the best data access governance possible to compliance and audit. Furthermore, Theom does not use a proxy-based architecture avoiding performance bottlenecks and extending one governance model from intro- to inter-company data exchanges.
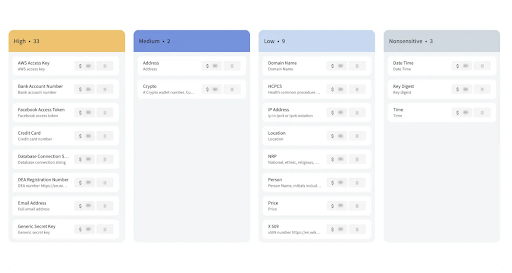
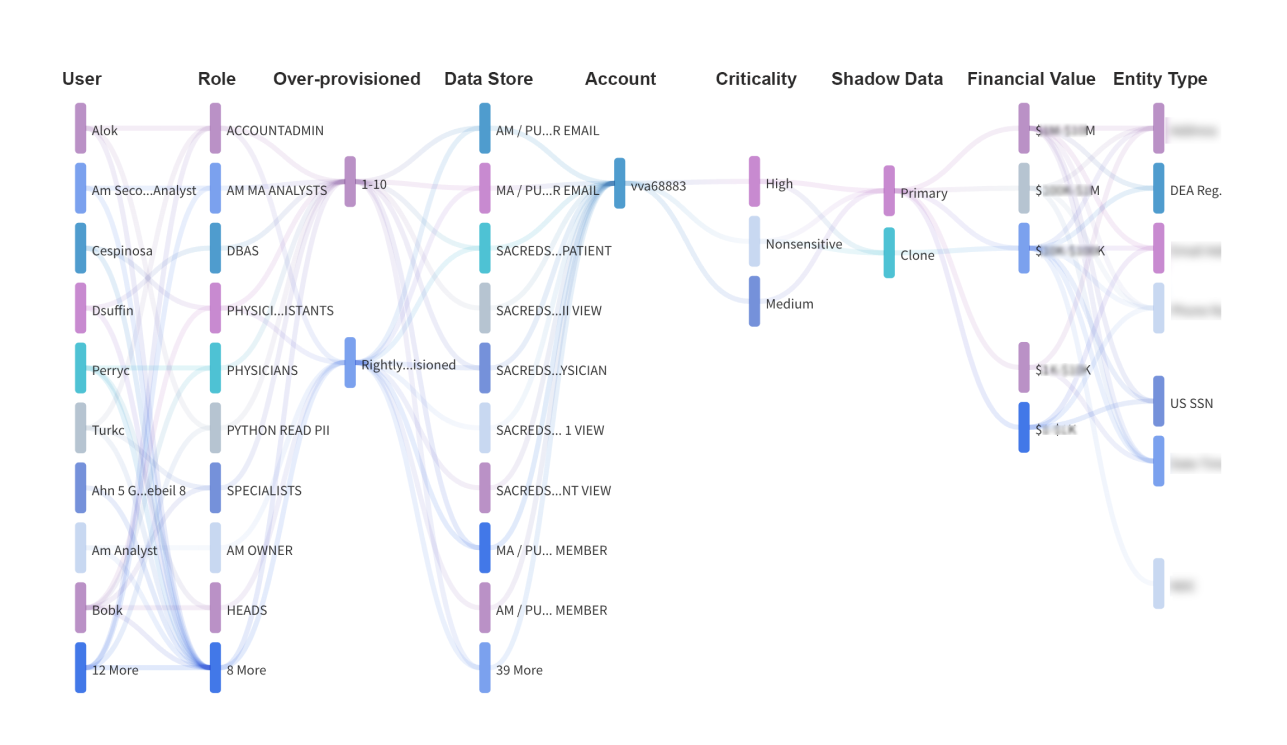
Discovery and Classification
“Not all data is created equally” - Theom's discovery and data classification modules help organizations identify and categorize sensitive data, ensuring proper access controls are in place. This process involves discovering and indexing data stored across various repositories on cloud environments and applying pre-defined classification rules to label and secure sensitive data automatically. It also involves establishing a monetary value of the data to assess the associated risk exposure properly. This will provide a prioritized map of vulnerabilities and suggests remediation to reduce potential exposures.
“You can’t always get what you want, you get what you need” (Rolling Stones) - Organizations undergo constant changes. Positions and org charts change as do project and team assignments. Unfortunately, access rights are frequently not updated creating a significantly larger attack surface than needed for any hacker. Theom automatically discovers and displays access rights that are over provisioned, have too many privileges or have not been used for longer periods of time. Subsequently, Theom will recommend actions to shrink wrap access rights in line with Zerotrust principles.
However, access is not a binary on/odd switch. It is much more the outcome of a multi dimensional process that addresses “ Who has accessed (or tried to access) what data at what time and from where and why? The multiple dimensions of this question and its dynamically changing nature show how data governance reaches machine scale and requires a software platform like Theom.



Detect and Stop Data Breaches
“See something, do something” – Theom's monitoring capabilities provide organizations with a clear view of all data access events. Once there is any abnormal activity, Theom takes action on potential data breach attacks using SIEM/SOAR integrations in a fully automated or hybrid approach. In line with customer preferences and incident severity, Theom can also take fully automated actions, e.g., immediate user shutdowns via API calls into an IAM system. Full audit trails of any such actions and alerts will be provided and could send to ticketing systems like ServiceNow. Lastly, Theom also correlates access behavior with many other data points enabling it to spot attempts to exfiltrate data already at the recon or staging phase. Therefore, Theom can already alert/take preventative action before an attempt to breach has even been launched. Theom is the only product that can detect attacks on cloud data lakes and warehouses and maps them to the MITRE &ATTACK framework.
Secure Data Sharing
Secure Data Sharing: Theom enables the secure sharing of data on Snowflake and Databricks by allowing enterprises to share data with external parties in a controlled and safe manner. Unlike older, proxy-based technologies that cannot enforce Data Governance beyond the initial proxy control point, Theom can fully extend its Data Governance into clean rooms. Theom Data Governance will be consistently applied to intra- and inter-company data access. This ability becomes increasingly important as inter-company data exchange becomes more prevalent.
Compliance and Reporting
“The proof is in the product” - organizations can generate comprehensive reports to demonstrate their compliance with various data protection regulations built on NIST, HIPAA, Hitrust, and CIS. Theom's reporting tools make it easy to track and manage access requests, identify potential violations, document remediations and maintain a transparent and auditable record of data access activities. Furthermore, the entire rules framework underlying Theom’s decision-making can be documented for regulatory and compliance purposes. Reports are also customizable to fit individual needs.

