Build good operational hygiene for data and access. Shrink wrap unwanted privileges continuously. Secure shadow and dark data.

Operation Hygiene for Data
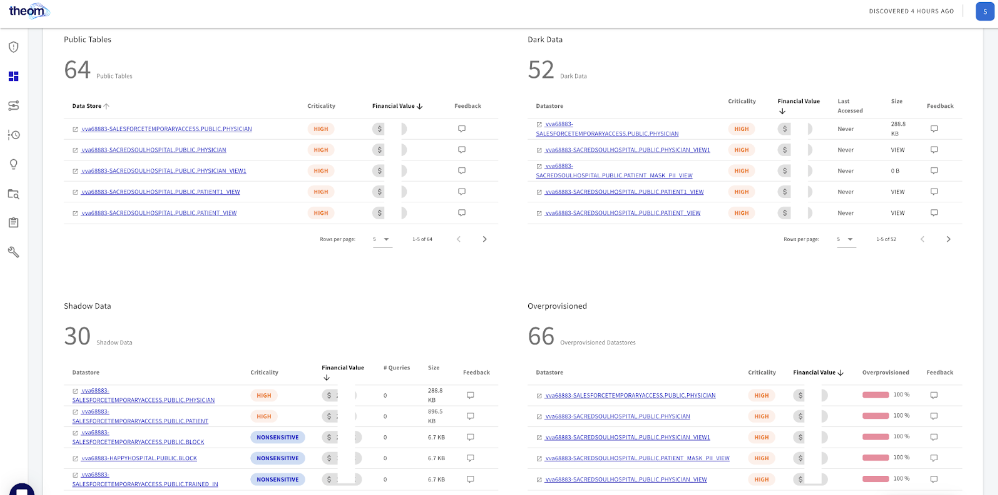
Data discovery is foundational to any robust data security practice. Organizations must find and manage all their data (sensitive or not) because you cannot protect what you can’t see. The unauthorized data replication/cloning for development, testing, or acceleration purposes seems far too common. This shadow data can fly under the data governance radar, creating substantial risk if not detected. Exporting data or metadata to external systems outside a customer’s jurisdiction usually raises concerns. Shadow data can also manifest as transient or permanent clones that deviate from the original copy of data. Dark data is data that has not been accessed for a long time (defined by the customer).
Organizations need help with shadow and dark data in the cloud - data that they are unaware of and possibly growing exponentially without the oversight of security and risk teams. Dark data tends to be unstructured and can contain sensitive information such as credit card numbers, medical beneficiary numbers, and developer secrets.
Managing shadow and dark data can eliminate many risks to enterprise access and sharing.
Theom is a data-centric cloud data protection platform. It maps cloud data environments and identifies sensitive data to be protected, including shadow and dark data. It pinpoints risks, including the impact on the business from cloud security risks. It automatically remediates these risks to ensure dark and shadow data are handled right and all accesses are controlled per the company’s data operational policies.
Operation Hygiene for Access
The questions “What data?” and “Who has access?” become even more complicated when the aperture is narrowed from the holistic to the atomic level, as the unit of labor for data access governance is rarely an entire data warehouse but individual cells or columns. Defining access rules down to individual cells has become necessary, not just in enterprises but inter enterprises where hundreds of millions of records are exchanged in clean rooms by allowing customers unique and fine-grained access to pieces of the same data set. Access rules are rarely static: employees and customers turn over, organizational charts change, and business processes get reorganized - updating systems is frequently challenging. Additionally, access rights get frequently defined rather loosely, i.e., employees receive access based on a role or their position in the organization chart and not based on the data itself and the business outcomes it drives. Every overprovisioned account is a substantial security risk.
Theom is an AI-driven data-centric access governance platform designed to provide organizations with a comprehensive solution for managing, controlling, and monitoring access to sensitive data. Using Theom, enterprises ensure that the right people have access to the right data at the right time, minimizing the risks of data breaches.
Understanding who can access the most sensitive data within the enterprise is a gap in today’s security tools. Further, understanding the reality of access, if the provisioned privilege for a user was used or not, is a much bigger issue. Theom's granular access control engine allows organizations to define specific permissions for each user, group, or role. This prevents unauthorized access and maintains a strict level of security by limiting access to only those who require it for their role. Administrators can easily configure and modify permissions as needed, ensuring a flexible and dynamic approach to access governance.
With Theom, enterprises can monitor and fix changes in access provisioning, role misuse, and atypical behavior of users. Further, identify compromised users, analyze potential blast radius, and prevent data breaches. For each access issue, Theom enables the quantification of potential liabilities based on criticality and $ value associated with the data. Theom has workflows to fix over-provisioning, so user permissions are shrink-wrapped, and principles of least privilege are implemented.

