Mitigate insider risks before they become threats with Theom’s native attack detection modules for Snowflake, Databricks, and Azure.

Insider Risk Management



When we ask “Who has access?” we assume that Who’s identity is well defined and that Who is a rational actor whose behavior is predictable and falls within well-established and understood guardrails. However, insider threats have become one of any enterprise's biggest and costliest risks. What happens if an insider starts exhibiting atypical behavior that has the potential to cause significant damage? What if a bad external actor managed to assume the legitimate identity of an insider or a trusted external partner for data exchange in a clean room? Insider threats usually try to leverage loosely defined and infrequently updated access rules. The size of the attack surface becomes a function of data access hygiene. Therefore, complete and ongoing audits of access rights are key. In addition, detecting atypical behavior requires knowledge of what is typical. Behavioristic baselining techniques will establish what a certain insider typically accesses. This can also be correlated with additional role-based intelligence, i.e., the definition of what is considered normal access for a user's role. Conflating all these data points will provide a detailed view of when insiders are not insiders anymore and are out to cause damage.
Theom is the industry’s only holistic data-centric access governance platform designed to continuously evaluate all access of your trusted workforce and applications on cloud data stores.
Using machine learning and mapping the MITRE ATT&CK framework natively into cloud data warehouses and data lakehouses, Theom enables you to gain data visibility, operationalize best practices, intervene early before an incident occurs, and advance your insider risk management program alongside your access governance and security initiatives.
First, Theom provides comprehensive visibility of access rights and data assets to tighten or revoke access rules where appropriate to reduce the attack surface for any insider attack.
Secondly, Theom seamlessly integrates contextual, human behavioral, and security monitoring to provide a single pane of glass—through which you can examine insider risks from every possible angle. Theom unifies insider risk management across clouds, mapping into MITRE ATT&CK framework and detecting malicious activity natively on data stores.
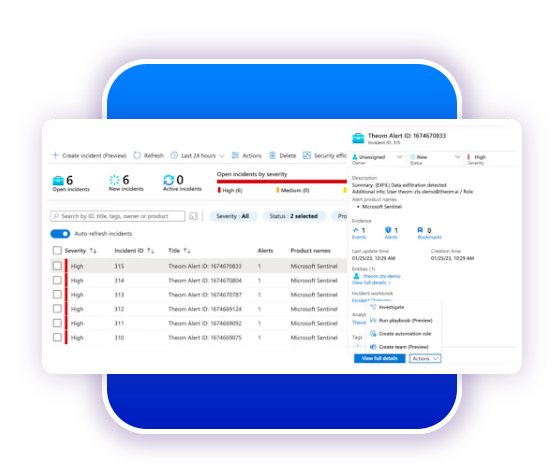
Theom also detects malicious use of native Snowflake capabilities, including load, query, clone, share, and export, to prevent data breaches. Furthermore, it understands how unity catalog and data sharing from Databricks can be protected natively. Abnormal accesses on your data pipeline identities or atypical user behaviors querying Parquet with SparkSQL are protected to prevent data breaches.
Theom enables access governance on Azure data stores. Integrated with Azure AD and Azure Sentinel, with Theom, you can detect and respond to data breach attempts working within the extensive Azure SIEM/SOAR/Identity infrastructure.
Lastly, Theom is embedded within your data lakes and warehouses and does not transfer any data out. Theom does not use a proxy or cross-account roles to mitigate insider risks. By operationalizing best practices in the context of understanding data, you can now manage insider risk and avoid large-scale incidents.

